| Traditional application |
Decentralized application |
| Users must create many username and password combinations for each service or application. Each combination must be managed and maintained. Also, each creation requires the user to provide important or unique information into the care of a third-party. |
Users create and own one or more identities. They use their identities with all applications and services. For example, a user could use the same identity for buying books online as they use for social media. |
| Multiple third-party applications and services store personal data from individual users in backend servers. These backend servers are under the control of the application or service. Users leaving the application leave their data behind. |
Personal information and data is encrypted and remains under the control of the user. Users leaving an application leave no data behind because none was stored with the application. |
| Multiple accounts across many servers make personal data subject to attack, misuse, and uncontrolled collection. |
Users can audit access to their data and know who accessed their data and which data were accessed. |
| Central authorities and middlemen control network access enabling them to censor applications and/or users that use them. |
Companies are developing blockchains that run over peer-to-peer networks. These future networks can make shutting down or entirely blocking a decentralized application close to impossible. |
The blockchain technology you build a DApp with determines the features available to your application.
## Try your first DApp by creating an identity
The Blockstack Web browser is a DApp for the web. Users can use it to create and
manage identities in the Blockstack Ecosystem. DApps built with the Blockstack
platform, use the on-boarding sequence provided by the browser to onboard their
users. Currently, users can create a Blockstack ID for free or buy their own
ID.
If you haven't already created your own Blockstack ID, do this now. As you
create an ID, consider what interactions are familiar to you from traditional
applications, and which are not.
{% include create_id.md %}
If you already have a Blockstack ID, launch the browser and try resetting it. Or
trying logging on from a device or browser software you haven't used before.
## Seeding DApp market with application mining
Blockchain applications are a new paradigm for both application developers and
application users. New paradigms in any market, think solar power or electric
vehicles, need private and private coalitions to grow. The centralized hosting
and services known as cloud computing were once new paradigms. It was the
investment of billions in funds and incentives from governments and private
companies that grew the cloud computing market.
{% include signature_fund.md %}
App Mining Eligibility Requirements
DApps that are eligible for application mining must:
- Implement Blockstack authentication
- Invite registration and use by the general public
Storing data in a Gaia storage hub is optional. Potentially in the future it may be required.
As you work through this Zero-to-DApp tutorial, you’ll build and deploy a sample
application that meets these requirements. While the application you build won't
be eligible for application mining, completing the tutorial makes you
eligible for a free, limited edition t-shirt:

You'll learn how to get your t-shirt in part 4 of this tutorial.
## Overview of the DApp you will build
You are going to build a DApp called AnimalKingdom. Animal Kingdom is a DApp for
the web. Users log into it and create an animal persona that rules over a
specific territory. The combination of persona and territory is a kingdom. Once
you create a kingdom, you can add subjects from other kingdoms.
The Animal Kingdom interacts with two Blockstack services, the Blockstack
Browser (https://browser.blockstack.org) and the Gaia data storage hub
(https://hub.blockstack.org/). The Blockstack Browser is itself
a DApp. The storage hub is purely a service without user-facing functionality.
The following table describes the key interactions and screens in the DApp.
| Click to enlarge |
Description |
|
|
Users log in (authenticate) with a Blockstack identity. By authenticating, the user gives the application the ability to get and put data in the user's Gaia storage hub. |
|
|
The Blockstack login dialogs are part of the Blockstack Browser which is itself
a DApp. Once a user authenticates, the DApp code automatically
returns them to the Kingdom they were attempting to enter. |
|
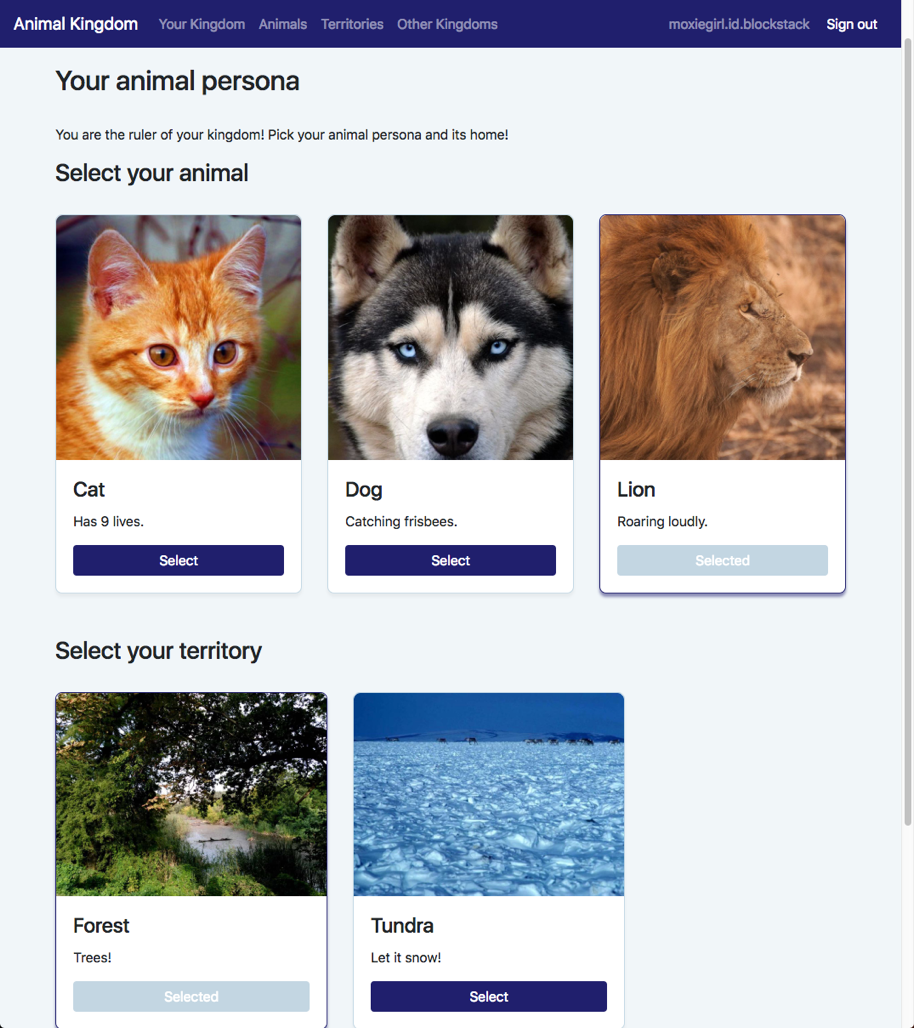
First-time visitors to a kingdom are prompted to create an animal persona and
a territory to rule. Once they make a selection, users click Done to create a
kingdom to rule. Behind the scenes, the data about the user's selection is stored in the user's Gaia hub.
|
| |
Each kingdom has animals and territories. Users can edit their original persona/animal combination. You'll learn how to modify the Animal Kingdom code to add new animals and territories. |
|
Users can add subjects from territories in their own Animal Kingdom. The DApp updates the user's GAI hub each time the user adds a subject. Users can also visit other Animal Kingdom installations and add subjects from these as well. You'll learn how to modify the Other Kingdoms available in your installation.
|
You can try a completed version of this application for yourself by using your
Blockstack identity to log into the